One of the requirements that Windows 11 brings with it to be installed is to have the so-called Trusted Platform Module, which is a chip that is designed to store passwords in a secure space. That is, on a separate chip that works as a kind of safe and not in the system BIOS/UEFI. well, two vulnerabilities in the TPM related to security could jeopardize such protection system.
One of the things that Microsoft wants most is to change the business model of Windows, from selling the operating system to giving it away, but charging royalties for applications and services through a store. This goes against the way of distributing content on PC and one of the obsessions of Redmond, and since Windows XP, is to try to control the ecosystem. His idea with the TPM? Have a large enough user base to force the TPM for security as much as possible. In this way they can force it in their applications such as Office, PC and Xbox games, etc.
The TPM has security issues
Traditionally, Microsoft’s strategy has been clear, first of all selling the software at a very low price until the competition can’t take it anymore and financially suffocates. The only business model that can survive these is that of free software, but in exchange for little by little in terms of improvements. The fact is that once those of Redmond have the monopoly or dominant market in something, they begin to raise prices. However, rampant PC piracy is a problem for them, hence requiring TPM for security to block such authorized copies.
That is, his tactic is to copy the model of the consoles to block unauthorized copies. In any case, they are within their right to defend their business model. However, the TPM in security is not entirely reliable, since two security problems have been discovered and they are not exactly small.
The problems are called CVE-2023-1017 and CVE-2023-1018, and are bugs that allow the system to write and read information beyond what would be allowed. Actually only two bytes, but it is enough to execute malicious commands that allow things like: access to protected information that is supposedly only available in this cryptoprocessor, that is, personal passwords, including bank passwords. Which makes this security problem a very serious problem.
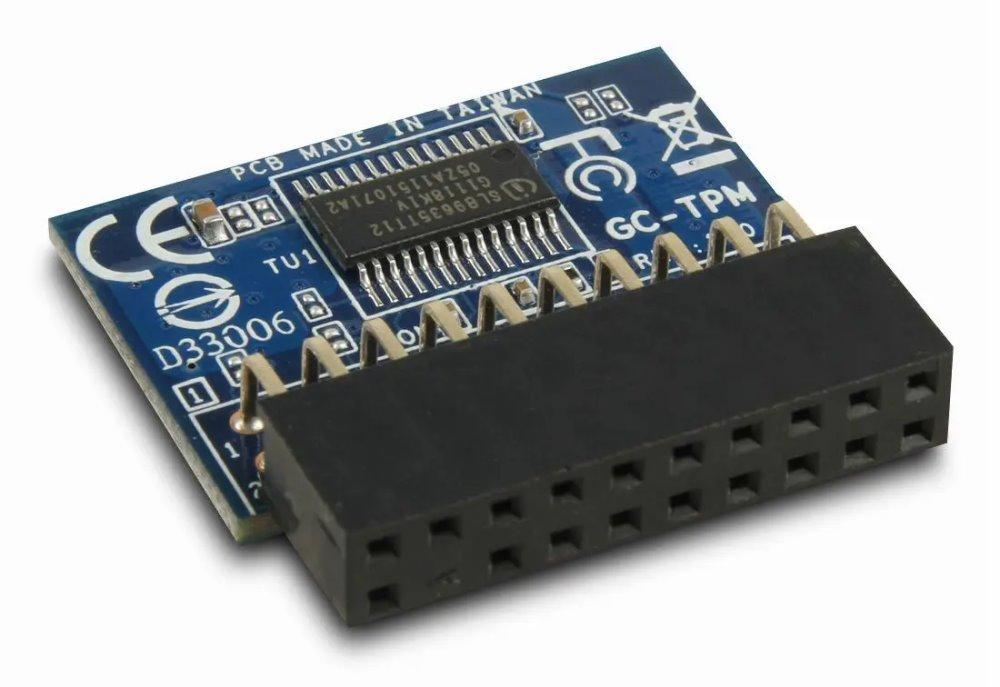
Is the Trusted Platform Module broken?
We must start from the fact that we are not talking about a software problem that can be easily solved with a patch since it is a hardware problem. Worst of all, what the TPM module executes has the highest degree of permissions of all in the system, so it is not only undetectable by the rest of the components, but any security flaw that is exploited will not cannot be stopped or by the kernel of the operating system. For further reference, we recommend reading our article on negative execution rings in order to understand the extent of the problem.
The post But, Windows 11 was not so secure? It seems not… appeared first on HardZone.